Outline of Article Content
1.
Error OverView: android webview showing net::ERR_CLEARTEXT_NOT_PERMITTED
2. Fix Cleartext Traffic Error in Android 9 Pie
2.1.
Network security configuration to
allow all Network connection types HTTP and HTTPS in Android (9) Pie
2.2. While allowing clear traffic to all domains by using above point: Google Play release APK will face
Security -> 1 known vulnerability detected in APK 51
2.3. Network security configuration
allows an app to permit cleartext traffic from a certain domains.
3. Gain More Understanding on Domain and Sub-Domain
1. Android Webview showing net::ERR_CLEARTEXT_NOT_PERMITTED:
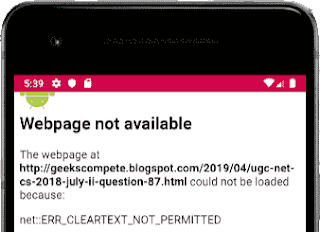 |
| android 9 webview showing net::ERR_CLEARTEXT_NOT_PERMITTED |
Webpage not available
The webpage at http://geekscompete.blogspot.com/2019/04/ugc-net-cs-2018-julpii-question-87.html could not be loaded because:
net::ERR_CLEARTEXT_NOT_PERMITTED
2. How to Fix net::err_cleartext_not_permitted Error in Android 9 Pie Webview
2.1 To allow all Network connection types HTTP and HTTPS in Android (9) Pie:
Need to follow the below two steps to Fix Cleartext Traffic Error in Android 9 Pie:
1) You now have to create a new file in your xml folder, file named
network_security_config just like the way you have named it in the
AndroidManifest.xml .
2) You have to set
android:networkSecurityConfig="@xml/network_security_config" in the application tag of your AndroidManifest.xml. This deceleration in your android application will allow cleartext traffic to all Network connection types in Android 9 Pie.
Step 1. Create a new file
res/xml/network_security_config.xml and the content of your file should be like this to enable all webview URL requests without encryptions:
Code for
network_security_config.xml:
<?xml version="1.0" encoding="utf-8"?>
<network-security-config>
<base-config cleartextTrafficPermitted="true">
<trust-anchors>
<certificates src="system" />
</trust-anchors>
</base-config>
</network-security-config>
Step 2. Add
network security config created above to your Android manifest file
under application tag.
Code for
AndroidManifest.xml:
<?xml version="1.0" encoding="utf-8"?>
<manifest xmlns:android="http://schemas.android.com/apk/res/android"
package="com.yourappname">
<uses-permission android:name="android.permission.INTERNET" />
<application
android:name=".MainApplication"
android:icon="@mipmap/ic_launcher"
android:label="@string/app_name"
android:largeHeap="true"
android:allowBackup="false"
android:supportsRtl="true"
android:networkSecurityConfig="@xml/network_security_config"
android:theme="@style/AppTheme">
</application>
</manifest>
2.2 Security -> 1 known vulnerability detected in APK 51
You may also face
warning messag as below on Google Play Console for your released APK/s
If you have allowed clear text traffic for all network traffic as suggested in step 2.1 of this article.
Cleartext traffic allowed for all domains
Detected in APK 48, 49, 50, 51
Your app's Network Security Configuration allows cleartext traffic for all domains. This could allow eavesdroppers to intercept data sent by your app. If that data is sensitive or user-identifiable it could impact the privacy of your users.
Consider only permitting encrypted traffic by setting the cleartextTrafficPermitted flag to false, or adding an encrypted policy for specific domains. Learn more
2.3 Network security configuration - allows an app to permit cleartext traffic to/from a specific domain/s
If you have some limited number of specific domains for which you want to allow clear traffic then use below content for your
res/xml/network_security_config.xml file with your domain/s specified:
Code for
network_security_config.xml:
<?xml version="1.0" encoding="utf-8"?>
<network-security-config>
<domain-config cleartextTrafficPermitted="true">
<domain includeSubdomains="true">geekscompete.com</domain>
<domain includeSubdomains="true">geekscompete.blogspot.com</domain>
</domain-config>
</network-security-config>
Understanding on domain and subdomain:
Lets say your main domain is as below:
geekscompete.com
For example, you could create a subdomain for gallery pictures on your site called "gallery" that is accessible through the URL
gallery.geekscompete.com in addition to
www.geekscompete.com/gallery.
You can also set even more specific area of interest on your sitepage for your site with new subdoamin like below:
info.blog.geekscompete.com
Example of subdomain for the above domain are:
www.geekscompete.com
blog.geekscompete.com
info.blog.geekscompete.com
gallery.geekscompete.com
See here,
The structure and components of a URL to better understand the concept of the subdomain
More about Network security configuration:
<network-security-config>
can contain below tags:
0 or 1 of <base-config>
Any number of <domain-config>
0 or 1 of <debug-overrides>
Here these tags are:
<base-config> is the default configuration set for all network connections whose destination is not covered by a <domain-config>.
<domain-config> is configuration to be used for network connections to specified destinations, as defined by the domain elements.
Any values that are not set in <base-config> will use the platform default values.
The default configuration for applications which targets Android 9 Pie (API level 28) and higher is as follows:
<base-config cleartextTrafficPermitted="false">
<trust-anchors>
<certificates src="system" />
</trust-anchors>
</base-config>
The default configuration for applications which targets Android 7.0 Nougat (API level 24) to Android 8.1 Oreo (API level 27) is as follows:
<base-config cleartextTrafficPermitted="true">
<trust-anchors>
<certificates src="system" />
</trust-anchors>
</base-config>
The default configuration for applications which targets Android 6.0 Marshmallow (API level 23) and lower is as follows:
<base-config cleartextTrafficPermitted="true">
<trust-anchors>
<certificates src="system" />
<certificates src="user" />
</trust-anchors>
</base-config>





